
Firm Management February 6, 2026
Wipfli Partners with The Caddie Network
Wipfli and The Caddie Network will bring to life the connection between elite caddies and trusted advisors.

Firm Management February 6, 2026
Wipfli and The Caddie Network will bring to life the connection between elite caddies and trusted advisors.
February 6, 2026
February 6, 2026
February 6, 2026
February 6, 2026
June 20, 2016
As always in dealing with sales tax, the specifics of sales taxes depend on the rules in the jurisdiction(s) where you are taxed. These can vary a great deal, so you need to know which specific rules will apply to you.

June 20, 2016
As the middle of the year approaches, it’s worth taking stock of remote sales tax. Numerous states have enacted or are considering legislation enabling them to collect sales and use tax revenue from remote retailers lacking a physical presence in the ...

June 17, 2016
At Scaling New Heights, Intuit announced a new partnership with ICBUSA, part of the Institute of Certified Bookkeepers (ICB), and Hubdoc.

June 14, 2016
When chief financial officers (CFOs) in a Robert Half Management Resources survey were asked to rate the level of difficulty their jobs pose now compared to five years ago, 66 percent of respondents said their roles are more challenging today, and 30 ...

June 14, 2016
No longer a cumbersome, expensive investment, modern accounting software is designed to appeal to the entrepreneur that has little time to spare on simply running a business, and would rather focus on growing that business.

June 14, 2016
While the reviews included in this issue offer a good selection of both on-premise and cloud products that can work well for small to mid-sized businesses, there are other alternatives available to accountants and CPA’s that wish to offer bookkeeping ...

June 13, 2016
Larger corporations with more complex needs may want to look into Vertex Indirect Tax from Vertex Inc. which offers a host of tax solutions including sales and use tax calculations, along with consumer use tax and VAT. Part of the O Series of ...
June 13, 2016
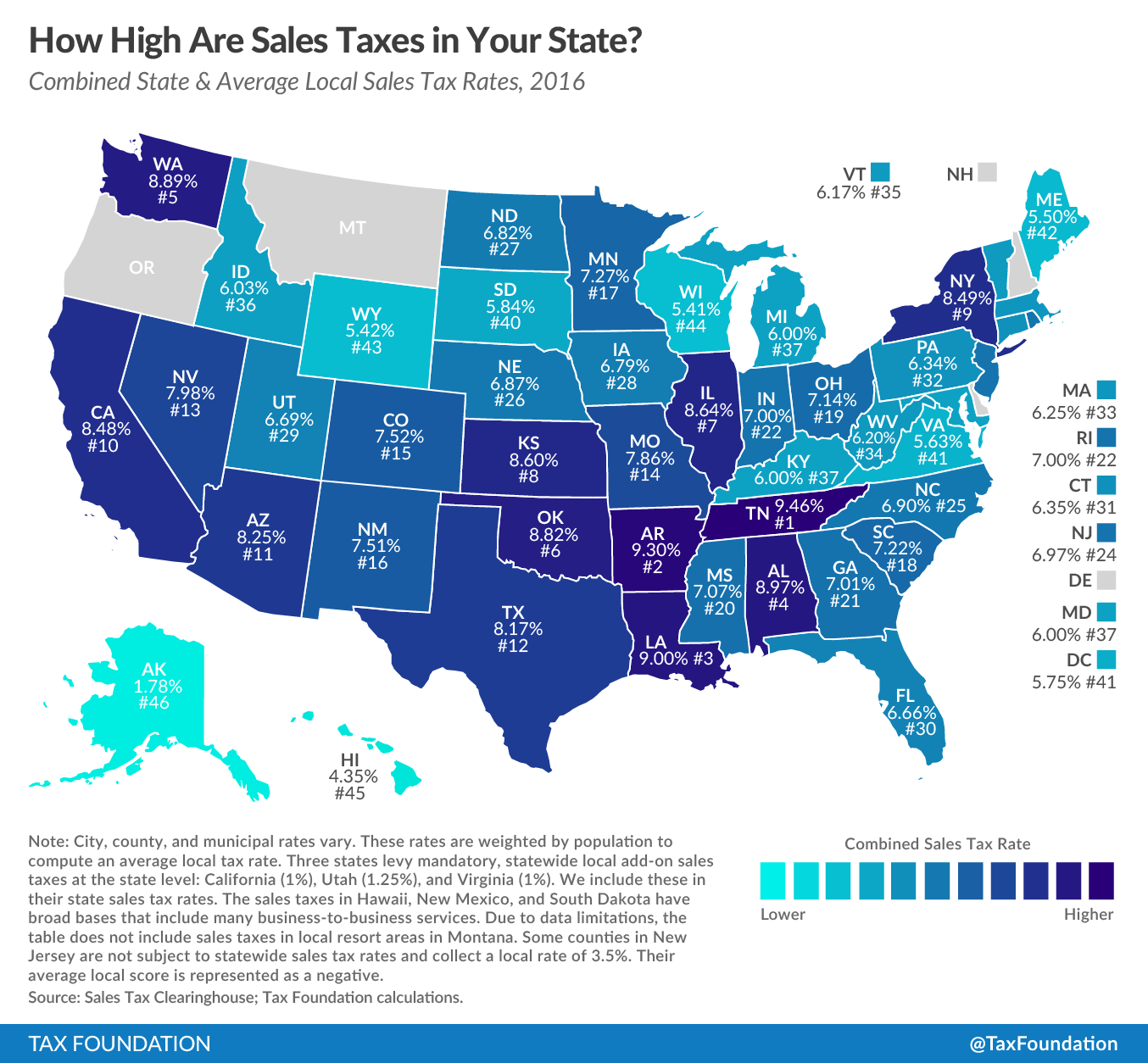
With the complicated rules, and the inordinate amount of time it would take today’s business owner to research and implement tax rates for cities, counties, states, and even countries, it’s imperative that today’s business owners invest in a software ...

June 10, 2016
Most of you who know me understand that I’ve had the privilege of having a long career in technology. The opportunities to help vendors build hardware products, as well as networking, productivity, accounting and document management software have been som

June 9, 2016
Whaling is a form of phishing attack where senior executives and others with access to valuable and sensitive data are sent very personal and well researched emails. The attacker may send the target an email that appears to be from someone they ...

May 25, 2016
Five IT Infrastructure and workstation trends for firms to consider as they evaluate system upgrades this summer.

May 24, 2016
I've been reporting on the accounting profession since Andersen was in the Big Five, Sarbanes and Oxley were just drinking buddies in DC, Enron was a company where great careers were made, and the PCAOB wasn't even a figment of anyone's imagination.